Vendor Security - How much diligence is due? (Evaluation Styles)
This is the second post in what will be a multi-part series that examines the question of how much rigour should be applied to ensuring a vendor’s security posture is adequate.
I hope that the first post in this series went a long way toward making the case that most companies would benefit from having an organised approach to managing security risks related to third-party products and services. If idea of building a formal process around vendor security management seems like too much for your situation, I would suggest that you cast a critical eye on your customer contracts, insurance policies, and regulatory frameworks; it is becoming increasingly common for vendor security management obligations to be included in data processing agreements and business relationships of all kinds.
Note: Everything I write is informational only, not professional advice. I offer only my personal opinions, experience, and research. Nothing I write represents the views of or has anything to do with any of my past or current employers or affiliates. You might also want to understand some of the personal biases that influence my thinking on this subject.
Evaluation styles
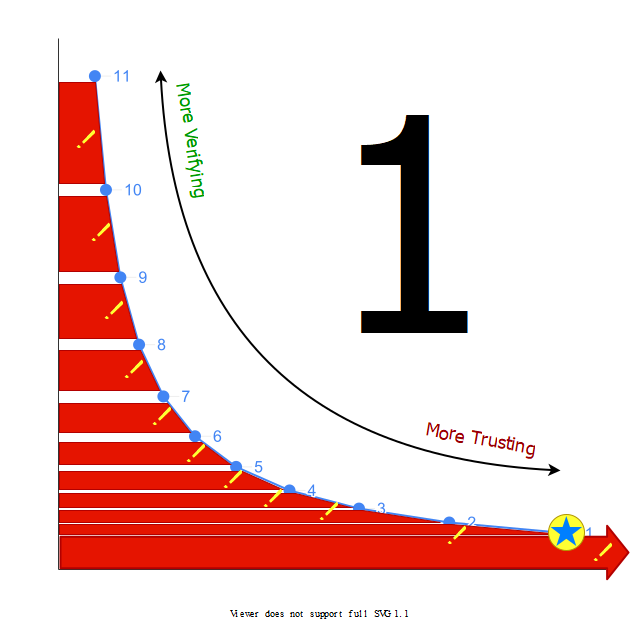
Before we dive into vendor security management process, let’s talk a little about a few of the possible options for examining a vendor’s approach to security - their “security posture” in cyber security lingo. In the examples below, I have ranked each evaluation method according a handy 11-point scale to show their relative balance between trusting a vendor and verifying their claims. These are not “real” numbers, just a way of demonstrating a few of the trade-offs involved. Why 11 points on the scale? I like prime numbers.
Let me explain a little about how to interpret one of these Trust & Verify scores by showing the diagram template:
The Trust & Verify scale goes from 1 (more trusting) to 11 (more verifying). You will note that the scale is not linear. Instead, it describes what mathematics aficionados call an “inverse relationship” and has a curve similar to what you would get if you graphed the function y=1/x. The purpose of showing this inverse relationship between trusting and verification is to show that there is a trade-off between the two. Comparing two specific rating examples will help to demonstrate that trade-off:
The diagram on the left shows the Trust & Verify score for a vendor security evaluation method that does some, but not much, checking of the vendor’s security posture.
Starting at the selected score (3), the area under the curve and extending to the low end of the scale (1) shows the relative cost of implementing the evaluation method. As indicated, low scores on the Trust & Verify scale have relatively low cost.
Starting at the selected score (3), the area to the left of the curve and extending to the high end of the scale (11) indicates the relative amount of risk that the vendor’s security posture does not meet your expectations. As indicated, low scores on the Trust & Verify scale show significant risk.
The diagram on the right shows the opposite case - a Trust & Verify score (9) for a vendor security evaluation method that does a great deal of verification of the vendor’s security posture. As you would expect, it shows that high scores indicate low risk and significant cost.
Examples
Now, let’s go through some representative approaches to evaluating a vendor’s cyber security posture, ranked by my estimate of their Trust & Verify score:
Blind Trust (T&V = 1)
The easiest and most obvious option for checking into a vendor’s security posture is simply not to check at all. If you like to walk around in the woods picking and eating mushrooms and fruit without even looking at them, this may be the choice for you - but probably not.
Faith in “The System” (T&V = 2)
Sometimes called “trusting your gut”, this method relies on assuming that people and companies generally do the right thing to protect themselves from liability and reputation damage. If we are honest, this is most people’s default approach to dealing with vendors and other third parties. Symptoms include clicking through license agreements without reading them, downloading open source software, and deciding that big brand names have far more to lose if something goes wrong than a user of their products and services.
Considered Selection (T&V = 4)
Often embedded into a formal procurement process as a “gate”, one-time evaluations are usually performed by people with some level of legal, privacy, and/or security expertise. Those experts request and evaluate licensing and other legal terms, vendor-supplied documentation of security controls, and other standard-issue business documents in which the company self-reports their attention to security. More sophisticated vendors will be able to provide customers with a prepared Standardized Information Gathering (SIG) Questionnaire by Shared Assessments. If enough money is involved, some vendors may be willing to answer a custom question set. To be effective, evaluations need to be done with details around what kind of data is involved and how it gets there. The result tends to be a yes/no decision, possibly with some restrictions around how the vendor’s products and services are to be used. Realistically, those restrictions are difficult to enforce.
Considered Selection with Audit (T&V = 6)
Performing an audit alongside a one-time evaluation is the most advanced of the “one and done” approaches to vendor security. Security audits, whether conducted by a third party or by the customer themselves, can be reassuring that good security controls and processes existed at the time of vendor selection. Keep in mind, however, that security is only as good as the people, process, and technology that maintain it. All of those things change with time.
Periodic Evaluation (T&V = 8)
In process design, there are only three important numbers: 0, 1, and ∞ (infinity). Whether you choose a vendor security review cycle lasting one year or one week, the overall process is the same. The steps are pretty much the same as the Considered Selection (one-time) evaluation method, but extra work needs to be done around actively tracking where and how the vendor’s products and services are used. I cannot stress enough the level of difficulty involved in maintaining the accuracy of that inventory. You also need a process to handle the inevitable discovery of someone using a product or service in an unapproved (probably dangerous) way.
Periodic Evaluation with Audit (T&V = 10)
Just like the one-time audit option mentioned above, you can require that vendors hire an independent auditor. You might also want the option to perform your own audit. In some cases, you might even require vendors to embed overseers directly into their development and operations groups. If that sounds a little unreal, consider that food safety inspectors often are embedded in meat plants where small mistakes can have huge negative impacts. Also take a look at some of the supervision and enforcement measures prescribed in the European Union’s proposed new version of the Directive on Security of Network and Information Systems (NIS 2 Directive), Chapter VI.
Build or Acquire (T&V = 11)
If your security requirements are higher than what a vendor can supply, you might want to think about whether involving a third-party product or service is a good idea at all. You always have the option of building a copycat … I mean, a customised in-house replacement. Bigger players might even attempt to acquire or merge with the vendor company itself. In either case, the time to improve the security posture of the resulting solution likely will be measured in years.
Summary
As you can see from the examples presented above, vendor security assurance methods involving any level of investigation beyond reading marketing materials requires considerable investment of time and informed, critical analysis. Every company needs to decide for itself what level of investment is appropriate for their circumstance, but across many business sectors, expectations around vendor security management are rising.
In particular, European privacy regulators have made it abundantly clear that where personal information is concerned, they expect very high standards indeed. One shining example of those high standards can be seen in the Penalty Notice handed down to British Airways after their vendor-related breach in 2018. (n.b. paragraphs 6.10 and following)
Next Steps
Regardless of which evaluation style(s) you choose, the overall process of evaluating vendor security is largely the same. In the next instalment of this series we will look at the overall process from a high level and set the stage for deep dives into the specific activities involved.